Cybersecurity: vigilance is the order of the day!

March 2017, France slowly enters the presidential election campaign. Candidates and voters pour their hearts out on the Internet. And now a controversy is swirling: some candidates’ websites have been hacked, or at least monitored. Two months earlier, similar rumors were circulating on the Web about the American presidential election. Also in the USA, a connected teddy bear made headlines in early March, when it was discovered that 800,000 user accounts for these stuffed animals had been hacked, enabling parents and children to send messages to each other via a telephone application, through the teddy bear. And these messages find their way onto the Web…
All this illustrates the extent to which malice and piracy have taken hold on the Internet. To paralyze these companies, cybercriminals have opted for DDoS(distributed denial of service), an attack classified as an advanced persistent threat(APT, read here). The principle: flood a computer server with mounds of incomprehensible requests, clogging up its response capabilities. As a result, customers no longer have access to the various services. What’s striking is the scale of the attack, multiplied tenfold by the use of a network of so-called “zombie” or “botnet” machines, specifically targeting connected objects, which lack the security required to fend off these assaults.

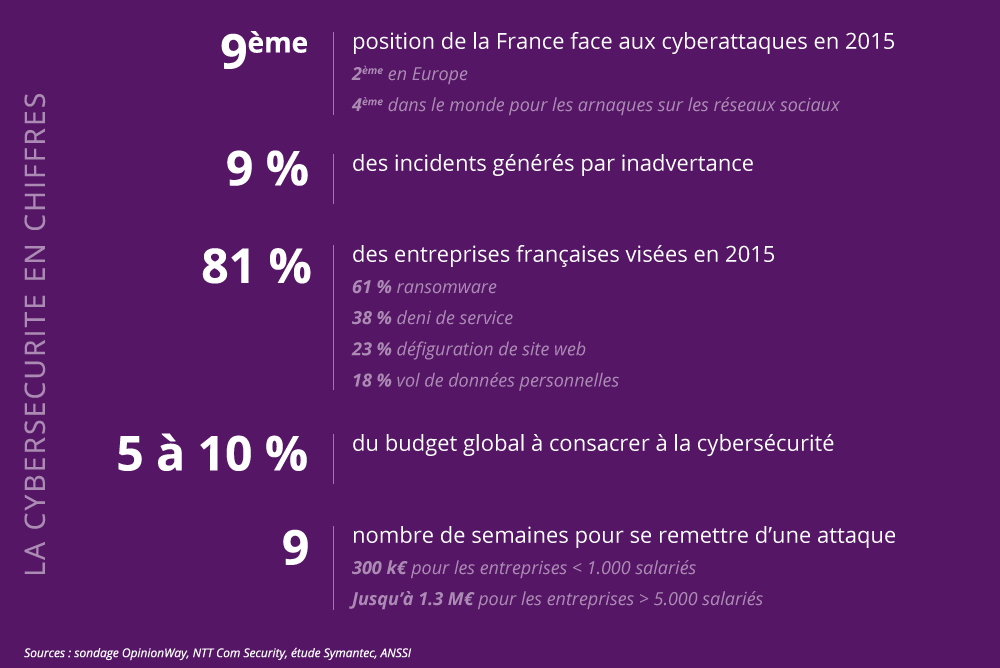
Today, ever greater dangers (social engineering, internal attacks, etc.) threaten both public and private organizations, using increasingly sophisticated means. Added to the blow to the credibility of an entity victimized by such a charge is the exorbitant cost of the necessary repairs. For example, following a monstrous hack suffered in 2015, the TV5Monde group had to spend more than 4.5 million euros to plug the breaches and devote 2.5 million euros each year to its security. With their limited resources, SMEs are increasingly targeted(see figures here), and pay a heavy price in the event of an attack.
Best practices
As François Lorek, who has been an auditor for AFNOR Certification since 2008, points out, “. Information security is broader than IT security, which is linked solely to resources, and looks at the problem as a whole in relation to the value of information, whether oral, paper or electronic. It concerns all entities, and particularly those holding sensitive assets such as third-party data, for example healthcare or banking data. In addition to this need for confidentiality, they must also ensure the availability and continuity of their systems, such as the cloud or e-mail, as well as their integrity: saved data must not be able to be erased or overwritten. “.
Information security, which has become a business of fear, requires the deployment of multiple, effective means. First of all, you need to look after your e-reputation. ” It’s all about anticipating risks by mapping them and using measurement and monitoring tools. An organization’s reputation is often built on the opinions expressed online about it, its products, and so on. Our NF Z74-501 standard, currently being transposed to ISO, ensures the reliability of consumer opinion processing. And our
guide FD Z 74-510 on e-reputation management
lists a number of best practices, ” explains Sylvie Arbouy, project manager at AFNOR Normalisation.
Because of the high stakes involved, some opt for a specific approach known as privacy by design, or taking privacy into account right from the design stage of a system or practice. ” Today, even the slightest piece of information can be used to profile individuals and, in some cases, maliciously harm their interests. Visit privacy by design guarantees end-to-end security during the design process for the entire data retention period. Impossible to invade users’ privacy “explains Frédéric Solbès, project manager at AFNOR Normalisation.
E-REPUTATION
Buy the “Online reputation management” guide
Computer hygiene
An increasingly precise arsenal of regulations and standards covers the issue of information security. For example, European Regulation 2016/679 on the protection of personal data, published in June 2016, will come into force in mid-2018. It focuses on information security to guarantee confidentiality, integrity and the absence of data leakage, etc. ” The European eIDAS regulation, in force since July 2016, covers digital identity and the security of electronic transactions,” adds Benoît Pellan, digital product manager at AFNOR Certification. It is the ANSSI (Agence nationale de la sécurité des systèmes d’information) that qualifies electronic signature and electronic seal certificate issuance services, following an audit. We will also be auditing the first certified health data hosts in accordance with the procedures defined in the order of January 12, a text stemming from the law of January 24, 2016 on the modernization of our healthcare system. “
In this case, the voluntary ISO/IEC 27001 standard deals specifically with information security. It enables us to set in motion a safety management approach tailored to the risks specific to each company. Everyone becomes aware of the need to respect safety measures to protect themselves and their organization. Just as the highway code does for a driver. Compliance with the principles of this voluntary standard guarantees good “IT hygiene”. Whether they’re called Chief Information Officer (CIO) or Chief Information Security Officer (CISO), operational staff are no longer alone: information security policies and investments are approved by senior management, with the aim of ensuring the long-term viability of the business. François Lorek goes one step further: ” Very complementary, the
ISO/IEC 20000-1
standard provides service providers with guidelines for guaranteeing IT security and continuity of service delivery.
Orange Business Services and BNP Paribas
(with its BP²I entity), among others, have obtained certification attesting that they apply this voluntary standard ,” says the auditor.
INFORMATION TECHNOLOGIES
Buy ISO/IEC 27001
Labels et référentiels
 Être certifié ISO 27001, sur la base de la norme volontaire du même nom, apporte beaucoup aux entités qui entreprennent la démarche, comme l’entreprise Iron Mountain, Orange Tunisie ou dernièrement, la Bourse de Tunis. Il existe en outre d’autres référentiels, comme SecNumCloud, développé par l’ANSSI et audité par AFNOR Certification. « Il vise les hébergeurs cloud et comporte de très fortes exigences de sécurité. La qualification de l’ANSSI délivrée après l’audit est un prérequis à l’obtention du label franco-allemand ESCloud, à vocation européenne. 2017 sera l’année des premières qualifications suite aux deux audits SecNumCloud que nous avons conduits en 2016 », explique Benoît Pellan.
Être certifié ISO 27001, sur la base de la norme volontaire du même nom, apporte beaucoup aux entités qui entreprennent la démarche, comme l’entreprise Iron Mountain, Orange Tunisie ou dernièrement, la Bourse de Tunis. Il existe en outre d’autres référentiels, comme SecNumCloud, développé par l’ANSSI et audité par AFNOR Certification. « Il vise les hébergeurs cloud et comporte de très fortes exigences de sécurité. La qualification de l’ANSSI délivrée après l’audit est un prérequis à l’obtention du label franco-allemand ESCloud, à vocation européenne. 2017 sera l’année des premières qualifications suite aux deux audits SecNumCloud que nous avons conduits en 2016 », explique Benoît Pellan.
De son côté, AFNOR Normalisation a élaboré un tout nouveau guide présentant l’apport précieux des normes volontaires pour la protection des données personnelles, sous l’égide de la commission de Frédéric Solbès. Autre ouvrage utile, 10 clés pour la sécurité de l’information, réédité en janvier 2017 par AFNOR Éditions, décrit avec pragmatisme les exigences d’un système de management de la sécurité. « Ce guide pratique démystifie les exigences de la norme ISO/IEC 27001, présente les nouveautés de la version 2013 et compte 32 fiches techniques », présente son auteur, Claude Pinet, qui a aussi participé à l’élaboration d’un outil d’auto-évaluation sur ce sujet dans la gamme BiVi d’AFNOR Editions. Cette norme fait aussi l’objet d’une formation proposée par AFNOR Compétences, conçue et animée par Vincent Iacolare : « Le but principal est de sensibiliser les participants à l’importance de la sécurité. Cependant, celle-ci ne doit pas tuer la performance, et toute démarche en ce sens doit donc être faite en bonne intelligence », commente l’expert formateur.
Autre cursus au catalogue d’AFNOR Compétences, le tout nouveau « Auditer la confiance numérique », cycle monté avec l’AFAI (Association française de l’audit et du conseil informatiques). La première session démarre fin avril. Comme l’explique l’un des intervenants, Jean-Yves Oberlé, « divisée en six modules, la formation traite de la culture du numérique. Elle pose les bases de la compréhension de cet environnement et sensibilise au risque numérique, ainsi qu’aux pratiques liées, dont les projets agiles ou les applications ». Dans un monde de plus en plus interconnecté, où la dépendance à l’informatique se renforce et le facteur humain joue un rôle essentiel, chacun doit donc s’impliquer dans une démarche affirmée de prévention, devenue incontournable. Il en va de notre sécurité.
INFORMATION SECURITY MANAGEMENT
Training with ISO 27001
3 QUESTIONS FOR HENRI HEUZE, HEAD OF INFORMATION SECURITY AT IRON MOUNTAIN
 Specialized in document management and conservation, your company has been AFAQ ISO 27001 in March 2016. Why take this step?
Specialized in document management and conservation, your company has been AFAQ ISO 27001 in March 2016. Why take this step?
Given our document archiving business, it was only natural to implement an information security management system. Other Group entities were already certified abroad, strengthening their credibility with customers and attracting new ones. This makes it possible to stand out from the competition. We are the first company in France to be certified in our field. Thanks to the audit, employees have a better understanding of the usefulness of processes (access control, traceability, etc.). Indeed, you can have very strict processes, but if you don’t understand them, they can be deviated from inadvertently: employee awareness reduces this risk.
What changes have you made?
An initial improvement cycle helped us prepare for the certification audit (analysis of existing systems, inventory of risks, risk management, etc.). An internal audit followed to measure the maturity of the management and information systems. After certification, we launched another cycle, with a new risk management plan. In January 2017, the certification scope will be extended from four to eight of the thirteen sites in France. AFNOR Certification has carried out an audit on this subject, and we are awaiting its conclusions.
What’s in it for you?
A better understanding of the Group’s policy, which is based on ISO/IEC 27001, among other standards. It also makes it easier to take part in tenders, and even provides a strong argument for winning them. Customer confidence has grown. If a customer visits or audits us, we’ll be able to provide the right answers, and even welcome them with great interest. In addition, being certified has enabled us to bring new skills and competencies to our staff. This has given visibility on service quality to customers, suppliers, public authorities, employees, the Group and shareholders.
Further training with AFNOR UK
In 2016, the UK launched its second strategic plan for cybersecurity, with a budget of £1.9 billion. In this country, which is heavily involved in this field, the BSI (British Standards Institution, the equivalent of AFNOR across the Channel) published a standard in May 2013, PAS 555, which aims to give structure to the governance and management of cybersecurity-related risks, by identifying best practices. PAS 555 focuses on the results of the strategy, which it evaluates,” explains Carolyn Jarvis, Head of AFNOR UK. ISO/IEC 27001, on the other hand, specifies the means to be put in place. These two tools are therefore highly complementary. AFNOR UK has set up a PAS 555 traininginternational deployment. It targets international auditors so that they can then carry out the training in their own countries. The first session takes place in February 2017, with more planned this year. “

Drawing up and monitoring standards
Get certified





